Welcome to our website on how to free yourself from Microsoft and the NSA by learning to use Linux and Libre Office and to our comprehensive step by step guide on learning how to install and use free open source tools (software) on your computer! Open source means the software is free and can be shared by anyone with anyone for any purpose. Open source is like a public library...free and open knowledge shared with the community for the common good. Free as in Freedom. No patents, no hassles, no barriers, no limits!
In June 2013, former NSA agent Edward Snowden confirmed that Microsoft works closely with the NSA. This website provides the shocking hidden details of that relationship and explains why it harms everyone from social activists to small business owners. If you are concerned about Microsoft handing over your data to the NSA, we are here to offer you a safer more secure option. If you have had enough of Windows 8 viruses, the Blue Screen of Death and Microsoft’s never ending stream of model changes and price increases, we will show you how to switch to a less expensive and more reliable alternative.
Our goal is to explain why you should install the free open source tools called Linux and Libre Office on your home, school and work computers – and then provide you with specific instructions on how to use these free open source tools to free yourself from the chains of Microsoft and the NSA.
But this website is about much more than simply learning Linux and Libre Office. Knowledge is power. If you really want to be free then it is important to learn the truth. Only the truth can set us free. The truth in this case is rather shocking. The truth is that there is a group of very wealthy powerful people who want to control the entire world – and to gain complete control, they intend to control both the internet and all of our computers. This book provides concrete evidence that at least some of the “crazy conspiracy theories” are true.
The shocking details revealed in this website include:
...Microsoft was “given” an exemption from the Sherman Antitrust Act in trade for giving the NSA access to all Windows computers.
...The NSA has access to every file on every one of the world’s two billion Windows computers – and has had this access since 1998!
.... The NSA used the “open back door” to Windows computers to launch a “cyber-attack” against Iranian nuclear power and oil plants in 2009 using an NSA created super virus called Flame.
... In early 2010, the Flame Super Virus escaped and began infecting commercial computers all over the world – and played a key role in causing the largest environmental disaster in the world – the BP Gulf Oil Spill.
... The Flame virus and its many cousins, which attack computers by pretending to be “Windows Updates,” have now infected millions of computers.
... As bad as all of this is the worst is yet to come. Microsoft’s latest operating system, Windows 8 comes with an extremely dangerous startup program called “UEFI: which is not only capable of remotely controlling every part of your computer – it is also capable of crashing the entire world economy!
“This wholesale invasion of American and foreign citizens privacy does not contribute to our security. Instead, it puts in danger the very liberties we are trying to protect.” Daniel Ellsberg June 10 2013
In April 2014, Microsoft will end support for Windows XP computers – leaving hundreds of millions of Windows users unprotected from Flame and other viruses. In just a few simple steps, you can protect your existing computer and the data stored on it. Now is the time to learn the full story about the relationship between Microsoft and the NSA so that you can protect yourself from the coming crash.
Who is this guy and why is he saying this crazy stuff?
Because many of the claims in our book and on this website may sound crazy, I would like to briefly explain who I am and why I wrote this book. Up until recently, I was a website consultant, community college instructor and a loyal user of the Microsoft Windows operating system and Microsoft Office word processing program. However, in 2012, Microsoft made a radical change to the Windows operating system when it replaced Windows XP and Windows 7 with an entirely different system Microsoft called Windows 8 and which they now call Windows 8.1 Blue. This new system is extremely difficult to learn and use – and it has several “features” which severely limit your freedom.
I was therefore in the process of writing a book called “Learn Linux and Libre Office – A Cure for the Windows 8 Blues” in order to give people an alternative to Windows 8.
Important Questions about Unusual Aspects of Windows 8
This research into strange aspects of Windows 8 and Windows 8.1 led me to seek out answers to a series of questions. These questions and their answers revealed several hidden connections between Microsoft and the NSA.
First, why has Microsoft been allowed to continue their monopoly of computer operating systems even after two federal judges found Microsoft guilty of repeatedly violating the Sherman Antitrust Act? The Microsoft Monopoly exemption occurred at the exact same time Microsoft gave the NSA access to all Windows computers. In fact, the Microsoft Monopoly exemption was granted by the same judge who later became the FISA court NSA judge! Could it be that our government secretly agreed to allow the Microsoft monopoly to continue in exchange for Microsoft giving the NSA access to all Windows computers?

Second, why would Microsoft risk their company and offend their users by moving away from a popular operating system like Windows 7 to an extremely unstable and complex operating system like Windows 8?
There were many strange things about Windows 8 that did not make sense. For example, why is the Windows 8 operating system actually two different operating systems with two different control panels and two different versions of the Internet Explorer web browser and two different sets of user interfaces? An operating system this complex has never existed before. Neither Windows XP nor Windows 7 had more than one control panel or more than one web browser. Also, why are our user names and passwords for Windows 8 now stored on a database at Microsoft rather than inside of our own computers as was the case with Windows 7? Such an invasion of privacy has never occurred before.
Third, why with Windows 8 and 8.1, was Microsoft forcing all computer manufacturers to move away from a simple stable computer startup program called BIOS to a new complex and unstable startup program called UEFI? Why should Microsoft even care what program computer manufacturers use to startup our computers? Why was the development of UEFI done in secret? Where did UEFI come from? Who created it? When was it created and what is its purpose? And why is UEFI ten times the size of BIOS if its only function is to tun on the computer and then hand the process over to the operating system?
Fourth, why does the UEFI startup program include a controversial feature called “Secure Boot”? Since its inception, Secure Boot has raised alarm bells among computer users because it gives Microsoft almost total control over our computers by preventing us from loading any program which is not approved by Microsoft. Members of the open source community have called this strange process “Restricted Boot” (see cartoon below). Where did secure boot come from? Who created it and what is its purpose?

Fifth, does Secure Boot included a “Windows 8 Kill Switch” which Microsoft (or the NSA) could use to kill your computer? Not only did the answer turn out to be yes, but the kill switch appears to be the main purpose of Windows 8!
Sixth, how does the Windows open back door work? it has been clear to many computer users that since 1998 Microsoft has used an “open back door” to make “updates” to our computers. This back door was created when Microsoft introduced Internet Explorer 4 and embedded this web browser into the Windows 98 operating system. I wanted to know how this back door worked, whether it could be turned off (it can’t) and what kind of changes it could make in your computer – even without your permission. What was the connection between the open back door and the increasing number of Windows Updates containing malicious code which crash Windows computers?

Seventh, what was the Flame virus and how is the Flame virus related to Windows Update problems? In June 2012, Microsoft admitted that a super virus named Flame was using the open back door to remotely attack Windows computers. This led me to research several more questions: What is the Flame virus? Who created it? When was it created? What is its purpose and how does it work? Also why have Microsoft’s monthly updates gone crazy during the past year? Why are there so many reports of these updates crashing computers? Are these security patches related to the Flame virus and/or the NSA?
Eighth, did the NSA Flame virus cause the BP Oil Disaster? Researching the history of the flame virus led to even more disturbing questions about the relationship between Microsoft and the NSA. Several newspaper reports confirmed that in 2009, Microsoft played a key role in the NSA attack on Iranian Nuclear and Oil Facilities via the development of the Stuxnet and Flame super viruses. Then, in 2010, the Flame virus escaped and began crashing not just Iranian oil facilities but lots of other oil facilities around the world.

I discovered evidence that the Flame virus led directly to the BP Gulf Oil Spill – the worse environmental disaster in the history of the world.

Ninth, is it possible that the Cyber War and the War on Terror are both fake? I discovered evidence that the so-called Cyberwar is fake. There have been cyber attacks. But they have not come from either the Iranians or the Chinese. Instead, there is evidence that nearly all computer attacks on US computers are initiated by the NSA - in order to create the illusion of a cyberwar. I also discovered evidence that the War on Terror is fake. There is no Al Qaeda. What passes for Al Qaeda is merely a branch of the CIA. Nearly all terrorist attacks appear to have originated with the CIA in order to create the illusion of a war on terror.
Al Qaeda appears to be simply a front for the CIA and CIA paid operatives. The ground to air missiles being used by these fake Al Qaeda groups were given to them by our own US government.
American tax payers appear to be funding both sides of the war on terror.

By June, 2013, I had uncovered some very disturbing answers to all of the above questions. Answers to all of these questions are provided in more detail in Chapters 1 and 2. Even before the Snowden revelations, I came to the conclusion that the real purpose of Windows 8, UEFI, Secure Boot and the open back door to the Windows operating system has little to do with what we have been told and more to do with Microsoft and the NSA taking over total control of our computers. I was in the process of finishing this book exposing the problems of Windows 8 and outlining the connection between Microsoft and the NSA.
Then on June 6, 2013, the incredible Edward Snowden articles exposing the relationship between Microsoft and the NSA started to appear.
We now know, thanks to the Snowden revelations in June 2013 that Big Brother is downloading not only all of our phone calls and emails – but every document in every Windows computer. One slide in particular indicated that in 2007 Microsoft helped the NSA jump start a secret mass surveillance program called PRISM.
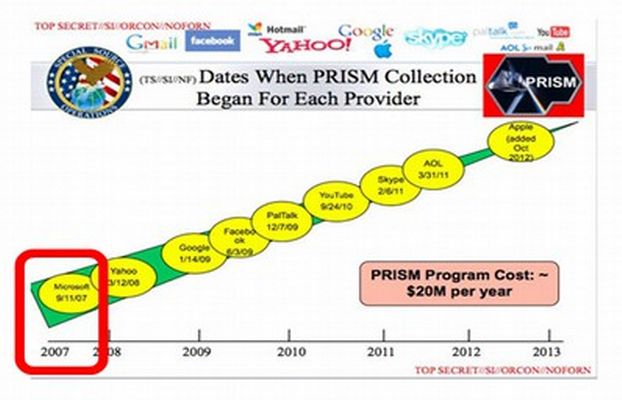
I was already aware that in 2007, shortly after joining the Prism program, Microsoft launched a parallel program to provide the NSA with a “kill switch” on all Windows 8 computers via a new secret startup program called UEFI with an ominous feature called Secure Boot.
After the Snowden revelations, I realized that the most important aspect of this book was to warn people about the dangers of Windows 8, UEFI and Secure Boot and provide computer users with a way to regain control over their computers by helping them switch to the Linux operating system. Thus, I changed the name of the book from “Learn Linux and Libre Office – A Cure for the Windows 8 Blues to “Free Yourself from Microsoft and the NSA – Learn Linux and Libre Office.”

The goal of this book is two fold: first to help you become more aware of the problems of using the Microsoft operating system – and especially the problems associated with Windows 8, UEFI and Secure Boot – and to provide you with step by step instructions on how to add and use the Linux operating system and the Libre Office word processing program.

Could All the Conspiracy Theories Actually be True?
As in the Wizard of Oz, we are told to ignore the man behind the curtain as our own government ignores international law and kidnaps the elected President of Bolivia and holds him prisoner while they search his plane for a person whose only crime was leaking the truth to the American people. The truth is that we are all being spied on and these massive spy programs are a clear violation of the 4th Amendment to the US Constitution.
“The 4th and 5th Amendments to the Constitution of my country, Article 12 of the Universal Declaration of Human Rights, and numerous statutes and treaties forbid such systems of massive, pervasive surveillance.” Edward Snowden, June 12 2013
As a reminder, here is what our US Constitution has to say about freedom of speech and the right to privacy.
AMENDMENT I... Congress shall make no law respecting an establishment of religion, or prohibiting the free exercise thereof; or abridging the freedom of speech, or of the press; or the right of the people peaceably to assemble, and to petition the government for a redress of grievances.
AMENDMENT IV... The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no warrants shall issue, but upon probable cause, supported by oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.
What Snowden is saying and what I also believe is that our allegiance should not be to a corrupt government or to any immoral laws. Rather we should uphold the Constitution of the United States and we should support the Universal Declaration of Human Rights.
Does the NSA control the Ministry of Truth?
As in the book 1984, power crazy people control the media. They control business. But their real objective is not merely to control knowledge and money – but to control people. How they control us is through something called the shock doctrine which is an endless war – a war against people, a war against our environment and a war against the truth. Because knowledge is power, these wealthy people want to control the internet. One way they control the transfer of knowledge is by waging a war against reporters and whistleblowers. Another way they plan to control the transfer of knowledge is by controlling all of our computers. They do this by controlling the backdoor to the Windows operating system on more than one billion Windows computers around the world. The best and easiest thing you can do to defeat their plan and to free yourself is by learning Linux, Libre Office and other free open source tools.

Try to imagine you are living in a world very different from what we were raised to believe, a world even worse than Orwell's 1984. Imagine a world in which the war on terror is fake. In this book, we provide evidence that the goal of the NSA is not to control terrorism – but to control and enslave people around the world. There are no weapons of mass destruction – only weapons of mass distraction.
War is Peace
Freedom is Slavery
Ignorance is Strength
George Orwell 1984
Imagine the possibility that the cyber war is fake. In this book, we provide evidence that the NSA not only has developed super bugs to attack other nations, but that it is also using those same super bugs to launch fake attacks on businesses here in America to make it look like there is a cyber war – when in fact the NSA is behind BOTH SIDES of the war – just like in the book 1984. Imagine a world where nearly everything you read in the newspaper and watch on TV news is fake. Imagine a world in which elections are sold to the highest bidder and political parties are simply friendly faces for Big Brother. The evidence is all around us and right in front of us. Think about the bank deregulation of 1999 with the repeal of the Glass Steagall Act – which led to the economic collapse of 2008 – which led to the multi-trillion dollar bailout of the “too-big-to-fail-and-too-big-to-jail” Wall Street banks. This bailout was accomplished by robbing trillions of dollars from the American people. The robbery is still going on.
Lies of the NSA
If you have any doubts left at all that our own government is lying to us about NSA spying, please watch the following three minute Youtube video produced by ProPublica. http://www.youtube.com/watch?v=eptZuXkUGmI
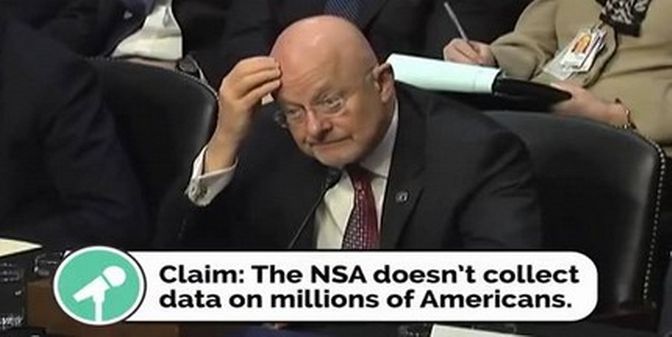
Oregon Senator Wyden asks a direct question: “Does the NSA collect data on millions of Americans?” James Clapper in an obvious act of perjury replied “No Sir.” What is most amazing about this lie is that James Clapper still has a job.
Meanwhile, the NSA corporate backed war machine uses fear to manipulate and control us.
NSA SHOCK DOCTRINE WARNING SCALE
SEVERE DANGER... Bombs will explode any minute!!!
Hide under your bed and trust us to protect you.
HIGH RISK OF IMMINENT ATTACK (or maybe an attack in the next week or so... especially if you live in Detroit)
Contact your Congressperson and ask them to vote for more funding for the NSA. Call now while you still can!
ELEVATED RISK OF SOMETHING BAD PERHAPS HAPPENING SOMEWHERE IN THE NEXT MONTH...
Stay indoors and report anyone wearing a suspicious backpack. Avoid traveling in a car, train, plane or boat.
ATTACK STILL POSSIBLE... BUT OK TO GO SHOPPING... Internet Chatter no longer indicates an attack will happen soon. Feel free to go into debt. How about buying a new computer?
In August 2013, our government announced the closing of 22 US Embassies and issued a world wide travel alert for the entire month of August - warning Americans not to travel – during the biggest travel month of the year. Supposedly this warning is due to the threat of a possible terrorist attack from Al Qaeda based on unknown information from a “very credible source.”
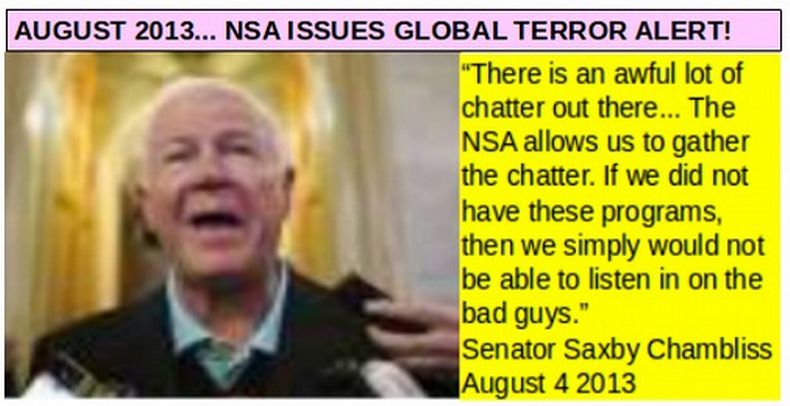
Supposedly, the timing of this threat is related to the end of the holy month of Ramadan and Laylet al-Qadr, or the Night of Power, one of the holiest moments on the Muslim calendar. In August, 2012, Iran supposedly used this day to launch a cyber attack on Saudi Oil computers. However, in this book, we provide evidence that the Saudi computer attack on the “Night of Power” in August 2012 was launched by our own NSA. Iran had nothing to do with it. There are several problems with this new warning from the NSA. First, the timing has nothing to do with Muslim Holidays and everything to do with funding the NSA. The warning came just days after Congress almost voted to defund the NSA spying program.

As for the “credible un-named source” one wonders if that refers to James Clapper – the head of US Spying who recently admitted to lying to Congress in the “least truthful” way - or was it the CIA paid taxi driver who warned about “weapons of mass destruction” a few years ago?
The real purpose of the attack – or threat of attack – is to scare the American people into providing hundreds of billions of additional tax dollars to the NSA.
NSA Attack on the First Amendment Freedom of Speech
On August 8, 2013, there was another shocking attack on the 1st and 4th Amendments. The email service used by Edward Snowden, Lavabit, was shut down by the NSA for refusing to hand all of their data over to the NSA. Until they were shut down by the NSA, Lavabit had 350,000 users – all of whom no longer have access to their email accounts. The NSA justifies this abuse with what they call the “Three Hop” Rule which they claim gives them the right to all of the data of anyone who has any relationship to anyone who has any relationship to an NSA suspect. Since Snowden might have some relationship to a terrorist and since the 350,000 Lavabit users are on the same email database as Snowden, the NSA gets to download all of the data of all 410,000 people.
|
"This experience has taught me one very important lesson: without congressional action or a strong judicial precedent, I would strongly recommend against anyone trusting their private data to a company with physical ties to the United States.” Ladar Levison, Founder of Lavabit |
Below is a link to one of the most shocking videos I have ever watched:
http://www.youtube.com/watch?v=Ui3KpztUzVg&feature=c4-overview-vl&list=PL50BDB9BCCFAF09CA
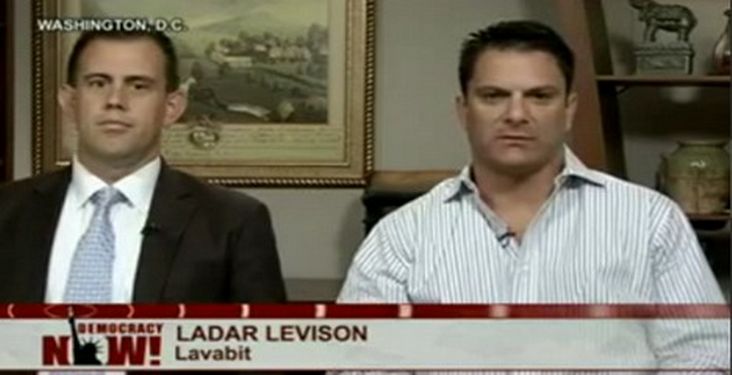
Levison added: “What I’m opposed to are blanket court orders granting government access to everything. If the American people knew what our government was doing, they would not be allowed to do it anymore. What we have seen in recent years is their willingness to use those laws in ways personally I consider to be unconstitutional, unethical and immoral."
Edward Snowden, speaking from Moscow correctly noted, “America cannot succeed as a country where individuals like Mr. Levison have to relocate their businesses abroad to be successful.” The next day, another US email encryption provider, Silent Circle, shut down. Another US “secure” email service, Hushmail, caved and handed over their database to the NSA. Once people realize that their data is not safe with Hushmail, they too will go out of business. The lesson here is that the only safety for your data is by moving your cloud data and email service to servers which are located outside of the United States.
Economic Suicide
The problem with NSA surveillance is that our entire economy depends upon email privacy for efficient communications. For the past 20 years, the one bright spot of the US economy has been our lead in technology and cloud computing. However, businesses and individuals do not want their data handed over to their competitors. They have seen how the NSA handed over Airbus data to Boeing. Businesses will increasingly migrate their data to places they view are safer. The systematic takeover or closure of companies such as Lavabit, Silent Circle, Hushmail, Microsoft, Google, Apple, AOL and all other “partners” of the NSA mean that all of these companies will eventually be driven out of business – because their business model cannot succeed when their potential customers know they are being run by and for the NSA. All of their employees will lose their jobs. Some economists have estimated that American technology businesses could lose over $100 billion in cloud computing contracts worldwide over the next three years as businesses move their data overseas to avoid the NSA. However, cloud contracts are just the tip of the iceberg. As people around the world realize that companies such as Microsoft and Apple cannot be trusted to protect their data or their privacy, the total economic loss to the US will be in the trillions of dollars and millions of US technology workers will likely lose their jobs – all thanks to the cyber monster called the NSA.
”The U.S. government, in its rush to spy on everybody, may end up killing our most productive industry. Lavabit may just be the canary in the coal mine.” Jennifer Granick Stanford Center for Internet and Society
On August 21, 2013, the German Federal Office for Security in Information Technology (BSI) warned citizens to avoid Windows 8 for being “an security risk.” An English summary of the article is at the following link.
http://www.testosteronepit.com/home/2013/8/21/leaked-german-government-warns-key-entities-not-to-use-windo.html
Rüdiger Weis, a professor at the Beuth University of Technology in Berlin, and a cryptographic expert, told Die Zeit in an interview that Microsoft wanted to completely change computing by integrating “a special surveillance chip” in every electronic device. Through that chip and the processes of Windows 8, particularly Secure Boot, “users largely lose control over their own hardware and software.”
With the 2008 bank bailout, the largest robbery in history occurred right in broad daylight. Since then, tens of millions of jobs have been transferred to sweatshops in China while entire American cities like Detroit have been destroyed and driven to bankruptcy. Will we now fall victim to an NSA induced recession?
Political Suicide
At the same time that the NSA is bringing down internet companies, it is also destroying freedom of the press. Reporters have been threatened with jail time for refusing to hand over their sources to the US government. In Great Britain, the government just forced the news agency, The Guardian, to destroy the hard drive containing information leaked to them by Edward Snowden. If we no longer have privacy or freedom of speech, how can any group critical of the government organize? How can any whistleblower safely contact any reporter? How can human rights groups get information from victims of human rights abuses? How can any client safely and privately communicate with any attorney? How can any patient privately consult with any doctor?

Legal Suicide... The End of the Rule of Law?
Also in August 2013, online open source legal firm, Groklaw, announced that they too are shutting down explaining that the work they do is simply not possible if they are under the control of the NSA. The American Civil Liberties Union and several other freedom groups have filed lawsuits trying to restore our 4th Amendment right to privacy.
Perhaps the most shocking of all of the revelations in August 2013 occurred with the release on August 20, 2013 of the 85 page FISA Court opinion which found that the NSA had violated the Bill of Rights “tens of thousands” of times.
http://www.scribd.com/doc/162016974/FISA-court-opinion-with-exemptions
Written by FISA Court judge John D. Bates on October 3, 2011, on page 16, the court noted that the NSA has repeatedly lied to the court about what it was doing:
“This Court is troubled that the governments revelations regarding NSA acquisition of internet transactions make the third instance in less than three years in which the government has disclosed a substantial misrepresentation regarding the scope of a major collection program... repeated inaccurate statements made in the governments submissions... frequently and systematically violating (the FISA Court orders).”
On Page 77, the court added: “The measures proposed by NSA for handling (emails of millions of Americans) tend to maximize rather than minimize the retention of non-target information.”
On Page 78, the court noted: “Each analyst... is left to apply the proposed minimization measures alone, from beginning to end, and without the benefit of his colleagues’ prior review... the governments proposed measures seem to enhance rather than reduce the risk of error... In sum, the NSA collection results in the acquisition of a very large number of Fourth Amendment protected communications that have no direct connection to any targeted facility and thus do not serve a national need.”
Basically, FISA court judge John D. Bates had assumed the government was telling the truth and then he found out the government was not telling the truth. In fact, the NSA had been keeping the FISA court in the dark since court oversight began in 2006. Judge Bates found that the NSA had violated the Fourth Amendment rights of Americans “tens of thousands of times” each year using the NSA’s own study (see page 41). In fact the actual number of violations may be in the hundreds of millions of times each year as we now know that the NSA is doing much more than they told Judge Bates.
On August 23 2013 we found out how the NSA got around restrictions placed on it by the FISA court was by paying its “Prism Partners” (including Microsoft) millions of dollars to do its dirty work for it.
The NSA paid and continues to pay millions of dollars to cover the costs of major internet corporations involved in the Prism surveillance program after a court ruled that some of the NSA's activities were unconstitutional. The material provides the first evidence of a financial relationship between the tech companies and the NSA. It is still not clear why it is okay for private companies like Microsoft to do things the NSA is not allowed to do. http://www.theguardian.com/world/2013/aug/23/nsa-prism-costs-tech-companies-paid
Also this summer, it was revealed at a Congressional hearing that the NSA has begun assembling scores of new cyber “offensive” and “defensive” teams, the agency’s most concrete step toward preparing the Pentagon and intelligence agencies for a new era of cyber warfare and computer conflict. These teams consist not only of NSA spies but also private corporate contractors

|
“The confluence of circumstances enabling mass surveillance has the potential to permanently imperil Americans' civil liberties. How we respond will determine whether we continue to function as a democracy.” |
Microsoft Blackmails Windows XP Users
The NSA wants total control over our computers. Their plan to gain access to all of our computers requires that Windows users “upgrade” from Windows XP to Windows 8. To make this happen, in April 2013, Microsoft announced that they will discontinue support for Windows XP beginning in April 2014. Since then, they have used a series of malicious Windows updates to sabotage Windows XP and Windows 7 computers in an attempt to force uses to replace their current computers with Windows 8. The only protection from these attacks is to turn off “Automatic Windows Updates” and install Linux as a dual boot. Sadly, Microsoft has sabotaged the Windows operating system in order to make it more difficult to install Linux as a dual boot – but we will show you how to get around these obstacles. The only way to take back control over your personal or business computer is to learn how to install and use Linux and Libre Office.
“This wholesale invasion of Americans' and foreign citizens' privacy does not contribute to our security; it puts in danger the very liberties we're trying to protect.”
Daniel Ellsberg June 10 2013
How this book is organized
This book is divided into ten chapters. Each chapter has four sections. The first chapter covers the rise of the Microsoft Monopoly and its hidden connections to the NSA. The second chapter covers the frightening consequences of this collusion between Microsoft and the NSA. The third chapter covers some of the major drawbacks of Windows 8. I want to make sure you are aware of all of the drawbacks of Windows 8 in order to inspire you to take the time to follow through with the rest of the book and actually install Linux on your computer. The fourth chapter covers the history of open source alternatives. The fifth chapter reviews how to download and use Linux Mint in a virtual box inside of your normal Windows computer. This will allow you to see how easy it is to use Linux and Libre Office without making any major changes to your current computer. The sixth chapter explains why and how to back up your computer and how to “dual boot” Linux with Windows. This may seem hard to believe but Microsoft is deliberately trying to crash your computer and prevent you from using Linux. You will see that Linux is not only easier than Windows, it is also much faster. The remaining chapters cover additional free open source programs to use with Linux to free yourself from Microsoft and the NSA.
This book is the text portion of our complete ten week 40 hour online course on using Linux and Libre Office. Each of the 40 chapters covers one hour in our online course. Each chapter covers one week in our ten week course. Our course also includes 40 videos demonstrating the skills discussed in each chapter, 40 activities to help you master these skills and 10 video conference classroom sessions, one hour per week for 10 weeks. If you are interested in taking our complete online course on using open source tools or learning more about our programs, visit our website, collegeintheclouds.org or email us for information on the next course offering. We have also posted this book on our book website, freeyourselffrommicrosoftandthensa.org in case you want to read the book online or refer your friends to it.
Other Books and Courses by David Spring
This book is the first book and course in our six book, six course series for sharing knowledge. In our books and courses you will learn how to use several free knowledge sharing tools including the Linux Operating System, Libre Office for word processing, Joomla for website management and Phoca Cart for Ecommerce.

For more information about all etn of our books and their related courses, visit our main website, collegeintheclouds.org. Here you will also find links to our Youtube channel with videos covering all of the topics in our books and courses. If you have any questions, feel free to post them on our website forum!
Are you ready to learn the power and freedom of Linux and Libre Office? Let’s get started!
David Spring, M.Ed.
September 11, 2013
Before moving on to Chapter One, we should first cover this basic question...
What is Linux?
Linux is a free computer operating system that works on almost any computer.
Linux runs 90% of all super computers – because it is the fastest in the world.
Linux runs 80% of the all stock markets – because it is the safest in existence.
Linux runs 70% of all smart phones - because it is simple and easy to learn.
Linux runs 60% of all Internet servers - because it is very dependable.
Linux runs 50% of all tablets - because it is the most versatile operating system. Linux is so versatile that it can run almost any Microsoft Windows program – including MS Office. Most important, Linux does not allow the NSA to access to the data on your computer. In short, Linux is the foundation for our global economy and the largest shared technology in history. Linux is also a free open source alternative to the Windows 8 Blues!

The general public has no idea what Unix is and does not care about the history of Linux. All they want is a simple dependable operating system they can use to run their computers and programs and files. The general public is more likely to be familiar with the name Linus because the great American physicist Linus Pauling was very well known. His name is pronounced Line – Us. Thus, most Americans are likely to pronounce Linux as Line – X because that is similar to Line- Us Pauling. In my opinion, with the open source community, either pronunciation is correct. This is because Open Source is all about the freedom to do whatever you want. So pronounce Linux any way you want. The important thing about Linux is not how we pronounce it – but that we actually learn how to use it.












